What is a Phishing Attack and How Can I Avoid Falling for Phishing Scams?

Picture this: You receive an email from your bank warning you about a breach in your account.
"Immediate action required," the email says, telling you that you must go to their website to verify your account's sensitive information. With the email looking as credible as can be and the situation dire, you don't hesitate to click the link. Providing vital account information such as answers to security questions and your social security number, you breathe a sigh of relief. With this information, the bank can secure your precious funds. Crisis averted!
There's just one detail missing: this was no email from the bank. In your rush to take immediate action, you failed to notice the typos in the email's copy, or that the website's URL was nothing like the bank's. You've given your vital data to a scam website - you've been phished.
Scammers can easily fool you in situations like this. You only want to keep your information and accounts, well, yours. And when you encounter an email like this - threatening harm and consequences while you're distracted - cybercriminals want you to fall right into their trap.
Fortunately, with the knowledge and foresight of phishing, you can recognize phishing attempts and prevent successful attacks against yourself and others.
In this blog, you'll learn exactly what phishing is, the common types and features of phishing attacks, and how you can recognize and evade phishing scams.
What is Phishing?
Phishing is a form of digital social engineering where scammers deceive others into giving them sensitive information. They do this by impersonating trustworthy individuals or organizations, such as coworkers or financial institutions, to trick people into thinking they are sending their information to the real deal.
If you've never heard of social engineering before, you may be wondering what it means. This is a type of manipulation that utilizes human interactions to convince people to perform certain actions or divulge information. In the heat of the moment, victims may not realize what's happening until it's too late.
By requesting information such as your birthday, address, social security number, and passwords, cybercriminals can steal your identity, transfer funds out of your accounts, and cause other harm online.
Now that you're familiar with the basics of phishing, let's look at some of the most prevalent types of phishing attacks.
Common Types of Phishing Attacks
Phishing attacks come in many different forms. Here are some of the ones you're likely to encounter.
- Email Phishing: Email phishing is one of the most prevalent types of attacks, and it comes in the form of an email message. This attack can target many people at once by sending fraudulent emails in bulk. Unlike legitimate emails, a lot of phishing emails have subtle differences that are key to discerning a phishing attempt from the real deal. These can include typos and poorly written copy in email messages, email addresses that differ from the legitimate sender, and message content instructing you to open attachments or click on shady links.
- Clone Phishing: This attack takes advantage of previously sent legitimate emails. In this instance, a sent email is resent with its links or attachments changed to phishing ones.
- Calendar Phishing: This attack disguises phishing links inside automatic calendar invites, such as those used on Google Calendar or Microsoft Outlook.
- Spear Phishing: Spear phishing is a more precise form of attack that targets specific individuals. While attacks such as email phishing can target a wide range of victims, this attack targets individuals by sending a message with their name, job position, or other specific data included. The personal aspect of the message can make the scammer's requests seem even more dangerous and urgent.
- Whaling Attack: This is a variation of spear phishing that specifically involves high-ranking individuals in an organization. In a whaling attack, cybercriminals act as important people, such as CEOs, and deceive users into sharing sensitive information with them. This type of attack pressures the victim into fulfilling the higher-ranking individual's request.
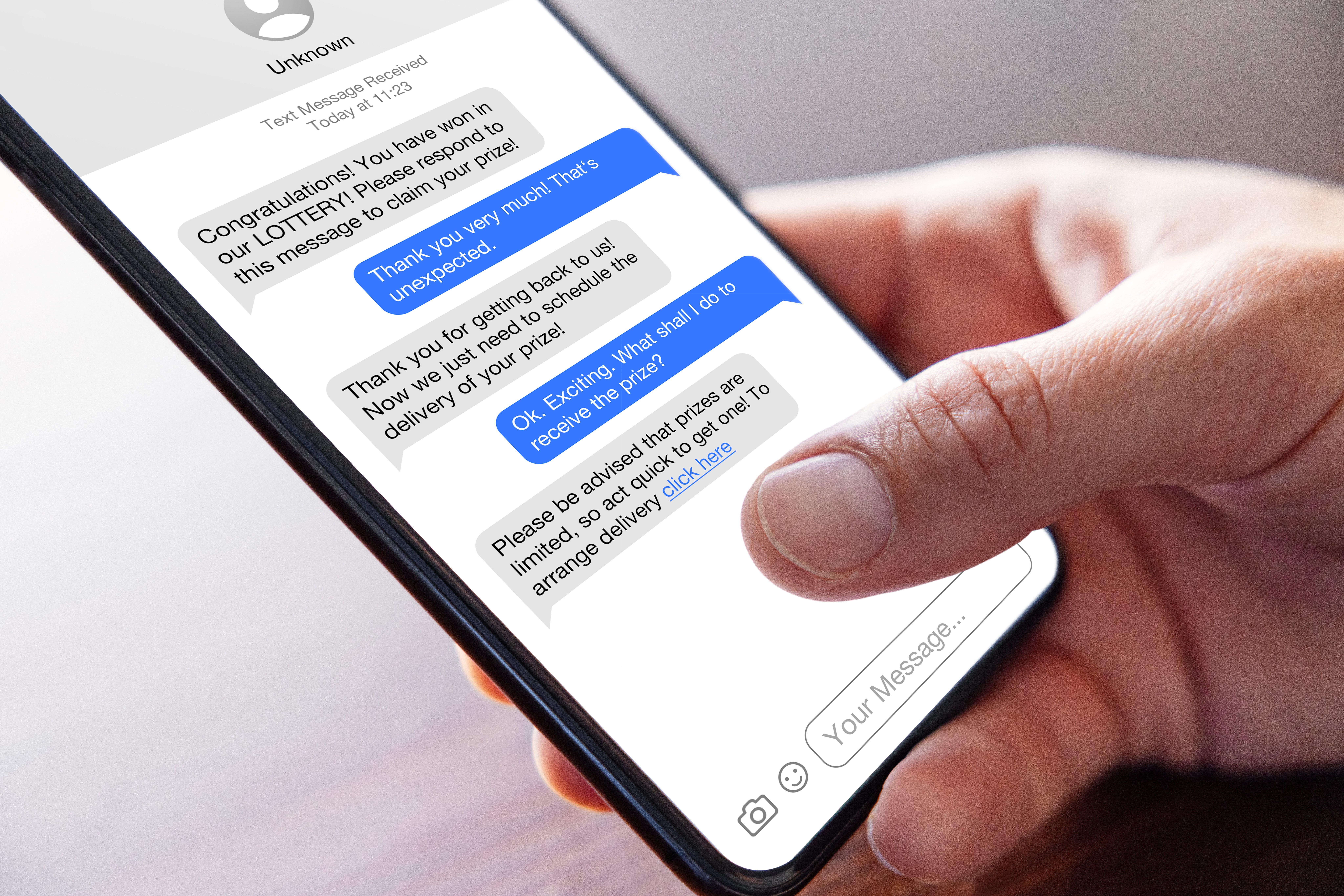
- SMS Phishing: SMS phishing utilizes text messages to get data from recipients. Phishing messages can contain phishing links or pretend to be from a trustworthy source.
- Voice Phishing: Voice phishing involves using phone calls and voicemail to request information from recipients. This kind of phishing is often combined with SMS phishing to act as a bank or other business that uses automated text messaging and voicemail.
With there being so many variations of phishing attacks, identifying them may sound like a daunting task. Have no fear; most of them share similarities that can make them easier to spot and avoid. Let's take a look.
Common Features of Phishing Scams
No matter how the message is delivered, the foundation of a phishing attack is the same: a perpetrator acts as a trustworthy source to trick you into sending them valuable information. Here are some typical characteristics of phishing scams that you can consider to identify a scam attempt.
- Sense of Urgency: Scammers use social engineering to intimidate you into giving up your information. They will threaten action against you, your data, and your accounts to get you to give in to their demands. Legitimate organizations don't threaten you if there's a problem - and ideally, your coworkers and other acquaintances wouldn't either.
- Mistakes: Real organizations would never send an email or text with many spelling or grammar mistakes. If the message's copy is full of errors, it probably wasn't written and approved by employees.
- Unusual Tone of Voice: If you get a message from someone that sounds or looks completely different from what you usually receive, it's likely to not be from them at all. Companies and individuals don't unexpectedly change their writing or design style.
- Incorrect Links: Fraudulent links are different from legitimate ones. You can spot a phishing URL by looking to see if it's encrypted using HTTPS protocols and has a trust or security seal such as a lock icon. In addition, fake links may contain misspellings or use symbols (such as a 0 instead of an o) and letter combinations (such as rn instead of m) to get as close as possible to a legitimate link.

Keep in mind that some perpetrators have sharpened up to these flaws. There are some phishing attempts that contain few mistakes, flawlessly weave a sense of urgency into the message copy, and use links that look nearly indistinguishable from authentic ones. You can be proactive and learn how to protect yourself and others from phishing attacks without ever encountering one - let's find out how.
How to Protect Yourself from Phishing Scams
There are many ways to educate and defend yourself from phishing attacks. Here are some ways you can learn about - and raise awareness of - these scams.
- Report Phishing: You can report dubious emails directly through an email client like Microsoft Outlook and Gmail. Emails can also be reported to organizations like the Federal Trade Commission (FTC) and Federal Bureau of Investigation (FBI). By letting others know about scam attempts, they'll be motivated to report scams they encounter themselves, and the attacks can be taken down and stopped.
- Awareness Training: Organizations can offer training to educate employees on phishing. Training can include reading documents, watching videos, taking quizzes, and going through simulations. With this knowledge, employees and organizations can greatly reduce the risk of losing important data in an attack. You can also educate yourself by keeping up to date on news about attacks.
- Phishing Simulations: Phishing simulators work with awareness training to send examples of phishing emails to an organization. The emails are sent internally and are used to see how employees react to the look and feel of a typical phishing attack. Employees who click on links or attachments are tracked and can receive additional training to reduce the risk of falling for a real attack in the future.
- Utilize Security Features: If scammers manage to get access to data such as your username and password, having security features like multi-factor authentication can prevent them from accessing your accounts. Furthermore, you can enable spam filters to stop phishing messages from even ending up in your inbox.
When all you want is to protect your data, the threat of phishing attacks can be scary. Now that you know the types and methods behind phishing attacks, you can take the right steps towards keeping yourself and the people you care about safe and prepared - crisis averted.
Feel like you could use a hand?
See what’s possible and give your teams the ability to create positive change.
Contact NowElevate your tech savvy! Warning: May cause increased knowledge.
Exclusive technology and development insights, tips, and podcasts await.


